IPS and AV - use it!
This post is coming on the back of the unfortunate situation that the Waikato DHB find itself in.
Apart from the disruption caused to the the public awaiting critical health services, and the potential loss of personal data and the massive amount of rework that is going to be needed to be done. It is a constant reminder that Network and IT security should not be seen as a reluctant cost, but something of value that enables your business/system to keep running.
The Internet is still a wild west, and as soon as you are connected you will be hit by automated probes and vulnerability scanners. It's like living in a bad neighborhood, someone will come past and rattle the locks and windows. If you give them a way in they will take it.
It looks like the DHB was hit by some variant of the the Conti/Ryuk or Valhalla malware. None of these are new and signatures have existing for several months. Yes zero-day vulnerabilities should be addressed ASAP, but a lot of the malware is known and simply takes advantages of systems that should have been patched.
Here are a few interesting pages that discuss these variants
- https://www.fortiguard.com/resources/threat-brief/2020/07/17/fortiguard-threat-intelligence-brief-july-17-2020
- https://www.carbonblack.com/blog/tau-threat-discovery-conti-ransomware/
- Wikipedia on Conti and Ryuk
Best Practice
At the very least here are a few best practices and things that you can do
At vBridge we offer a Firewall-as-a-Service solution that is based on Enterprise grade Fortinet firewalls, and we want to make sure that all our customers are aware of the features and really should use them.
Most/all routers/firewalls offer ACL based protection. This is simply allowing or denying traffic based on IP address and port information. But in this day and age that is simply not enough.
A few months ago I touched on securing your outbound rules, and that needs to be re-iterated here. Don't use open DNS recursors. Use filtered services or DNS Profiles, block traffic to Botnets or Websites that are security risks. This is more and more important with BYOD and more businesses opening networks to use Cloud Services and Modern Desktop environments.
But really don't forget about the inbound rules.
We are not just talking about opening up your required server ports. Even on that port there is addition steps that you should be taking. In Fortinet speak these are referred to as Security Profiles.
Intrusion Prevention
- Enable IPS scanning at the network edge for all services.
- Because it is critical to guard against attacks on services that you make available to the public, configure IPS signatures to block matching signatures. For example, if you have a web server, configure the action of web server signatures to Block.
- Create and use security profiles with specific signatures and anomalies you need per-interface and per-rule.
- Only use predefined or generic profiles as a convenient shortcut to supply immediate protection, you should create profiles to suit your network environment.
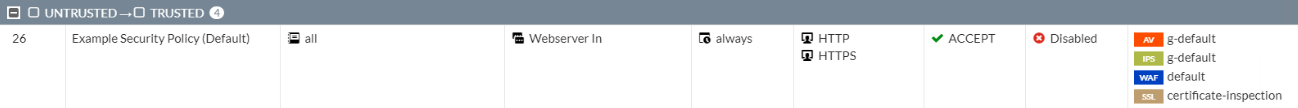
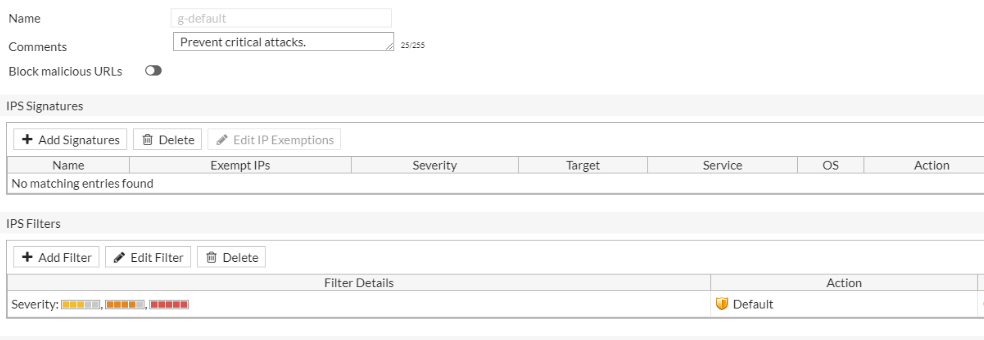
While default can get you started, it is better to create your own profile that is more specific to the destination service. i.e there is no point scanning for Linux attacks if your server is a MS Windows box. At this point you can also add in a bunch of rate based signature protections
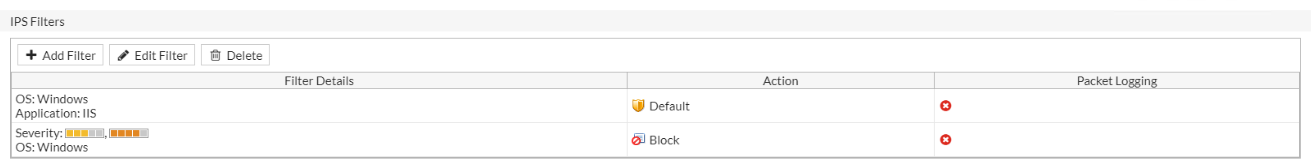
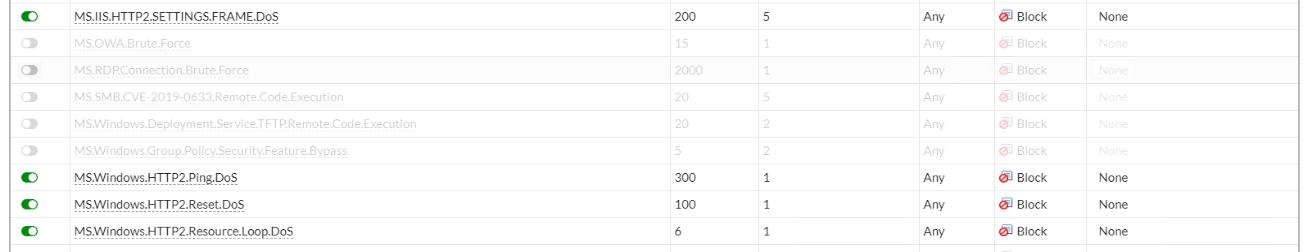
It won't take long before you see the traffic being dropped and protecting your servers.
Anti Virus
- Enable antivirus scanning at the network edge for all services.
- Enable only the protocols you need to scan. If you have antivirus scans occurring on the SMTP server, it is redundant to have scanning occur on the FortiGate unit as well.
- Reduce the maximum file size to be scanned. Viruses usually travel in small files of around 1 to 2 megabytes.
- Do not quarantine files unless you regularly monitor and review them. This is otherwise a waste of space and impacts performance.
- Examine antivirus reports and log messages periodically. Take particular notice of repeated detections. For example, repeated virus detection in SMTP traffic could indicate a system on your network is infected and is attempting to contact other systems to spread the infection using a mass mailer.
The challenge with AV is where to deploy it. Yes we can deploy on the FW, but for example if you are allowing SSL/TLS traffic out to https sites without doing proxy/offload/deep ssl inspection, then it is going to be of limited use. Any virus payload itself will be encrypted.
For additional information please see the Fortigate admin guides, Cookbook or the free NSE Training. Or give vBridge support a call.
Don't Forget the basics
- Keep your devices up to date and secure. Yes this becomes a challenge if you are dependent on old legacy software that requires old OS/sw to run (ActiveX/Adobe Flash anyone?) But there were reasons why these platforms were deprecated. Many hacks are as a result of known malware or take advantage of known security vulnerabilities that should have been addressed.
- Keep all your staff trained in network security awareness. Human compromise is by far the most common way for the bad guys to get in.
- Segregate and separate your network. Relying on Edge/border firewalls is not sufficient. You also need to limit and inspect traffic inside your network to prevent malware spreading. Take special care on alerts that come from 'trusted networks', they may indicate a compromised computer.
- Maintain endpoint security. Antivirus and Malware scanners are a must. Anything from MS Windows defender through to advanced EDR products like Carbon Black or Crowdstrike.
vBridge do not charge extra to enable Security Policies and advanced features. We maintain our Fortiguard subscriptions and receive all the AV/IPS and Botnet signature updates as soon as they are available. Please use them!
