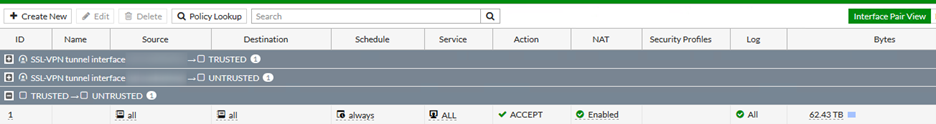
Outbound ANY-ANY rules are bad
One thing that irks me a bit is the number of firewall setups that have rules for allow all traffic out to the internet.
Most home routers come this way. You expect to be able to plug in and go without your router getting in the way. They just do NAT, and you’re off.
Notice I say router – and not firewall.
A lot of corporates and business also seem to seem to follow this pattern and just allow all traffic out.
Now, you may ask – “Why is this a problem? I don’t care what my staff do on the Internet?”
Well it’s all about protection (for you and the rest of the Internet) and if/when you are compromised, then limiting the impact of that issue.
Most people understand about limiting inbound traffic, and protecting Internet facing servers with IPS (Intrusion Prevention System) or WAF (Web Application Firewall), but why limit outbound?
Most compromises are caused by users inadvertently letting the malware in. Either clicking on a malicious link or opening a suspect attachment or being phished.
There are a few ways to address this
- IT Security training and awareness
- Having a segmented network
- Having good detection systems
- Limiting outbound traffic from networks
There’s a lot more to it than that, but I’m just concentrating on the last point here. There is a reason why the default deny policy on a Fortigate goes both ways.
- (and this has been round for many years). Prevent SPAM. Most ISPs these days even go to the extent of blacking outbound to port 25 (SMTP) from their networks, only allowing access to their official mail relays. But there should be no reason for individual PCs to send email directly.
- Prevent malware from “Calling Home”. If a piece of malware is running, then usually one of the first things they do is log back to a Command and Control network. These can we web based or IRC chat or any method. But simple malware itself doesn’t do much. They usually reach out to download something more sinister (e.g ransomware file encryptors). Stop that, you limit the damage.
- Prevent Amplification attacks. These are seeming harmless for one user or compromised host, but cause big problems for victims targeted by DDOS. Thousands of compromised hosts all sending a small amount of spoofed UDP traffic, can bring a target down by saturating their network circuits. Common forms of amplification attacks include DNS and NTP.
All of these are pretty easy to do something about and leave your network (and the Internet) in a better place.
- Limit outbound traffic to that which is needed. You may decide that HTTP/HTTPS out to everywhere is appropriate for you, but block other ports.
- Limit DNS/NTP to known/trusted servers.
- Use the DNS Filters and Website Classifications that come on a Fortigate to protect you where ACLs fail. This is a really strong feature on the Fortigates with UTM subscriptions, Fortiguard maintain IP lists of botnets and C&C servers. All of these can just be blocked. They also maintain category listings of most websites out there and you can use this to block known malicious sites that have been tagged as such.
Below is a very simple example and took less than 10 minutes to setup from scratch.
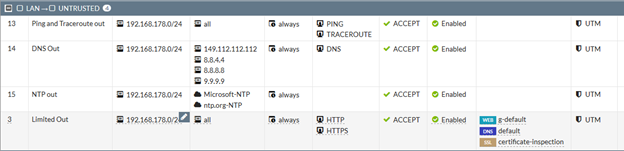
- Allow outbound ping (ICMP type 8 echo) and traceroute for network testing (maybe there is another blog post in why all ICMP is not bad)
- Restrict source IP addresses to your internal subnet. Why you may ask, all my internal computers _have_ to be on internal subnets to work? Because this blocks any packets with spoofed source addresses.
- Limit outbound DNS to Quad9 (Quad 9 is a free DNS recursive service – like Googles 8.8.8.8, but one that also filters out known bad domains and IPs). Simple case here defining the destination, for clarity.
- Outbound NTP limited to local ntp.org and windows time. Having accurate clocks on computers is important. This uses predefined Internet Services, so you don’t even need to look these up!
- Allow HTTP and HTTPS out – but use security profiles. I’m not making decisions on what you want to browse on the web.
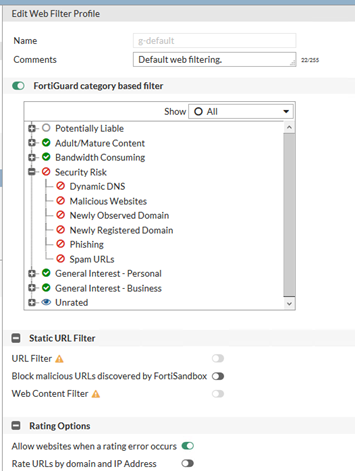
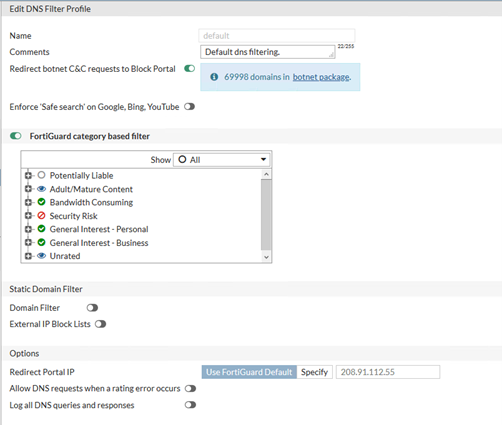
Under Network Interfaces
- Edit WAN interface to block outgoing connections to known botnets.
That took only a few minutes to setup. I’m not saying it’s complete by any stretch of the imagination. But it’s a start. And hopefully I won’t see many more rules like this