All your log are belong to us
Do you syslog?? Yes, well have I got a solution for you! vRealize Log Insight / Log Insight / or even vRLI in its abreviated form is a very capable option with a whole lot of functionality from VMware. It can be a simple syslog target or it can be grown into a fully functional SIEM if you have the need and / or time.
We, here at vBridge have a metric sh*te ton of devices that are capable of sending data to a syslog collector. Lets face it, an aggregator of some sort is needed unless you want to spend your time trawling through hundreds of different management tools, each with their own take on how best to present things. Or perhaps you found the unicorn 🦄 ....... that elusive Single Pain of Glass, no ....... I didn't think so! Having previously used a third party vendor for this we decided it was time to bring it back inhouse.
Deployed as a virtual appliance Log Insight is simple to get up and running and provides operational visibility along with query based alerting to assist with troubleshooting and analysis. You can look at ingestion rates etc and scale the size of the deployment to suit your needs or even deploy a clustered solution if required making it highly scalable. We decided to deploy two standalone instances (one in each of our Datacentre hosting locations Auckland and Christchurch) and configure forwarding between them. Data ingested in one instance is tagged and forwarded to the other meaning we can login to either and search for what we need (note, custom rules allow us to exclude data already forwarded being re-forwarded back to its original source which would be bad 🙈).
Speaking of forwarding, another niche use case for vRLI is to use it as a filter for 3rd party SIEM products like Splunk / QRadar / LogRhythm, some of whom charge / license on volume of data ingested....only forward what you need (or more importantly want to pay for).
To get a wee bit nerdy for a minute, Log Insight is compliant with a bunch of Syslog related RFC's (6587, 5424, and 3164 ) and supports both ingestion by the cfapi and syslog protocols (various ports: 514/TCP, 1514/TCP, 514/UDP, 6514 SSL/TCP, 9000 CFAPI and 9543 CFAPI/SSL).
Content Packs
These provide preconfigured dashboards with queries and alerts from a range of vendors and make life simple when you want to get started interpreting data. A simple right click and install and your ready to go (assuming you've already directed your syslog feed to Log Insight that is). For a full list of the available content packs have a look here.

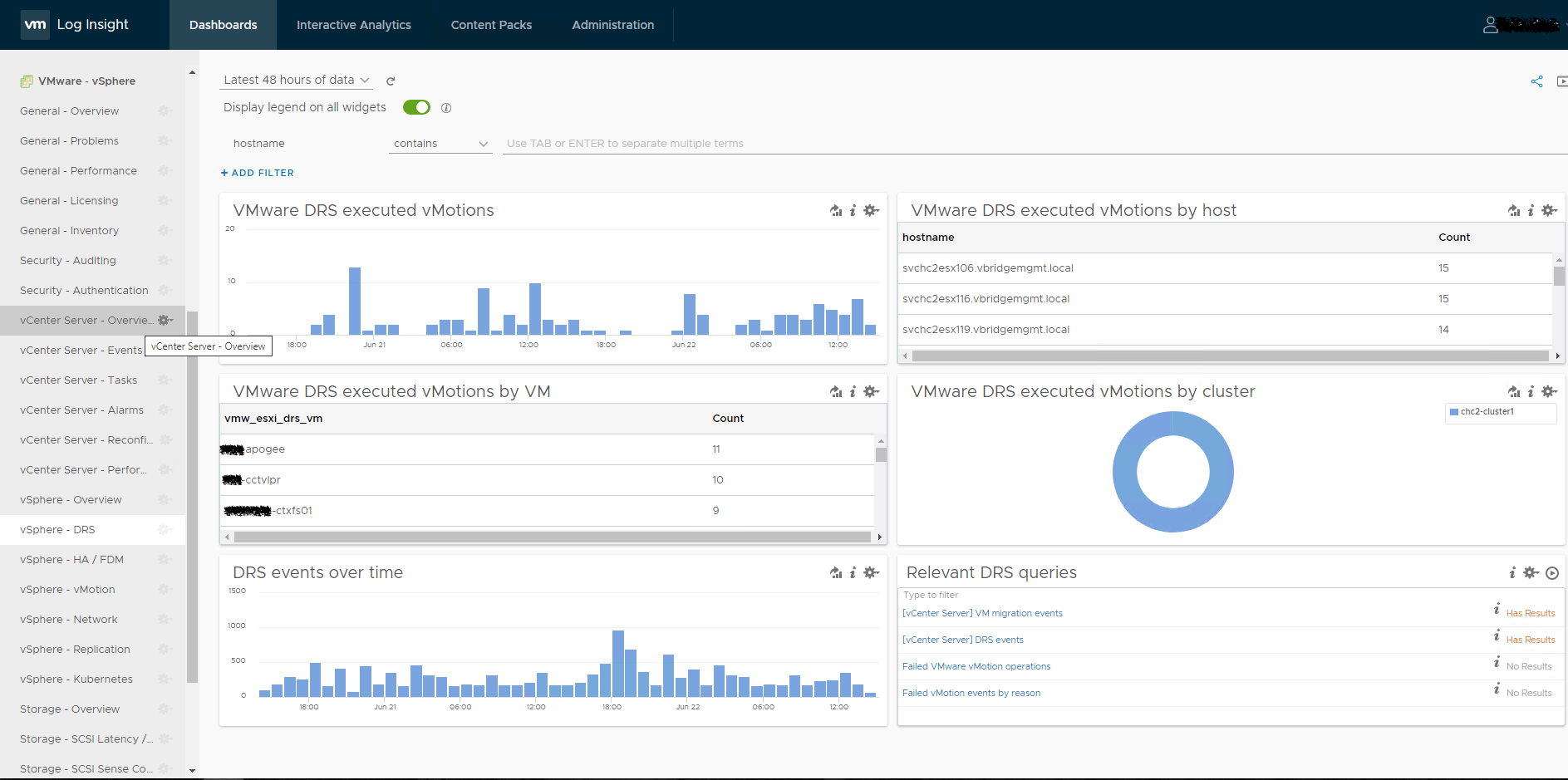
Dashboards
Dashboards are an important piece of the puzzle. Whether you want a general overview, some performance data or need to get into troubleshooting, the dashboards are a good place to start. These can be used to generate a read only URL for sharing or you can even put a dashboard into presentation mode if you happen to want a NOC like screen continually scrolling info.....
The Secret Sauce 🔥
Ok, so not that secret, but the Interactive Analytics and the power of Extracted fields are really where Log Insight shines. Simply jump in and just start typing anything of interest into the search field. There is a handy drop down box with pre-defined time slices to narrow your search (Latest 5 minutes, hour, 6 hours, 24 hours etc) and also the ability to choose a custom time range. Stack your filers, exclude events, and auto generate graphs to visualise whatever it is your after.
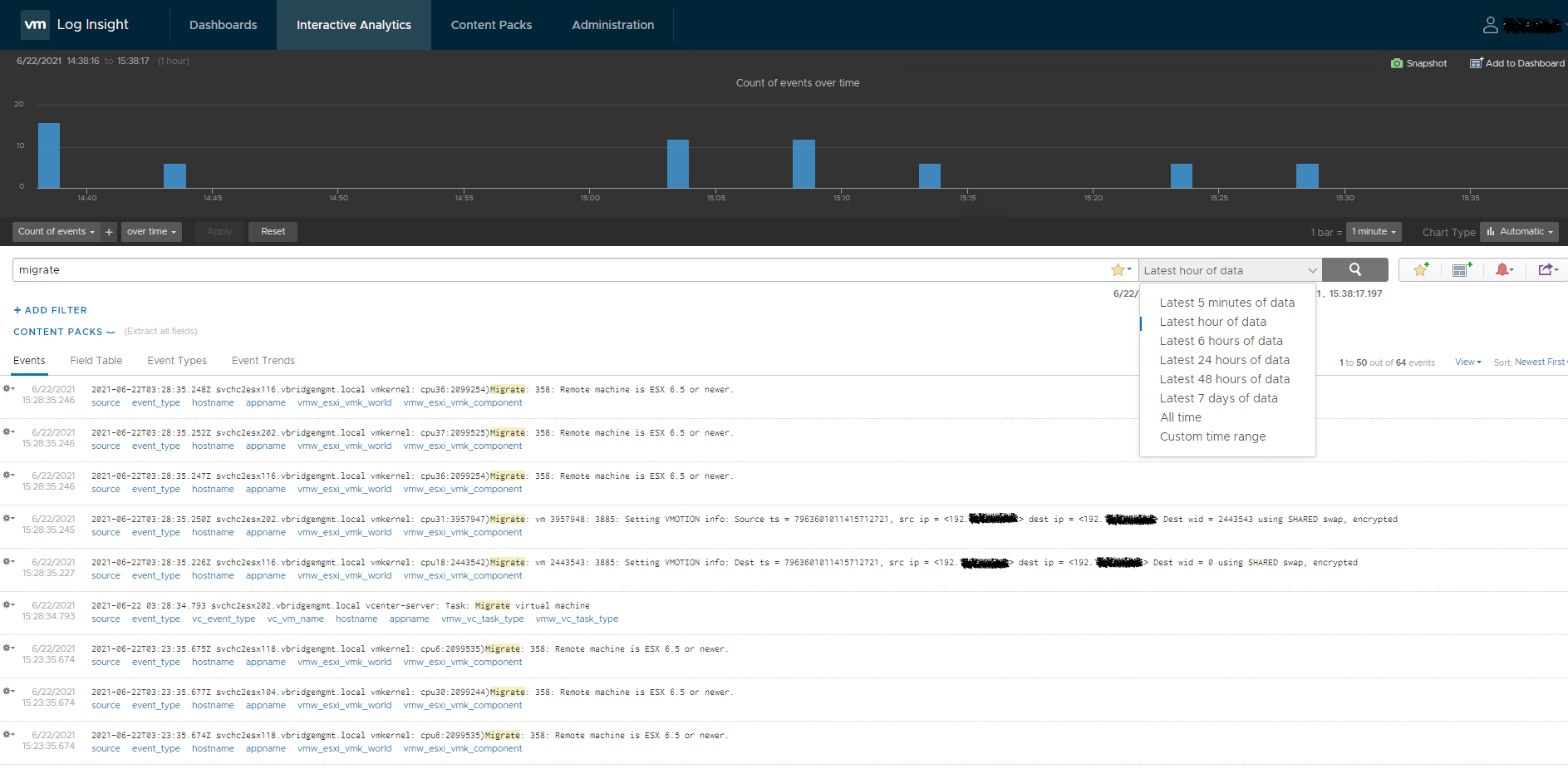
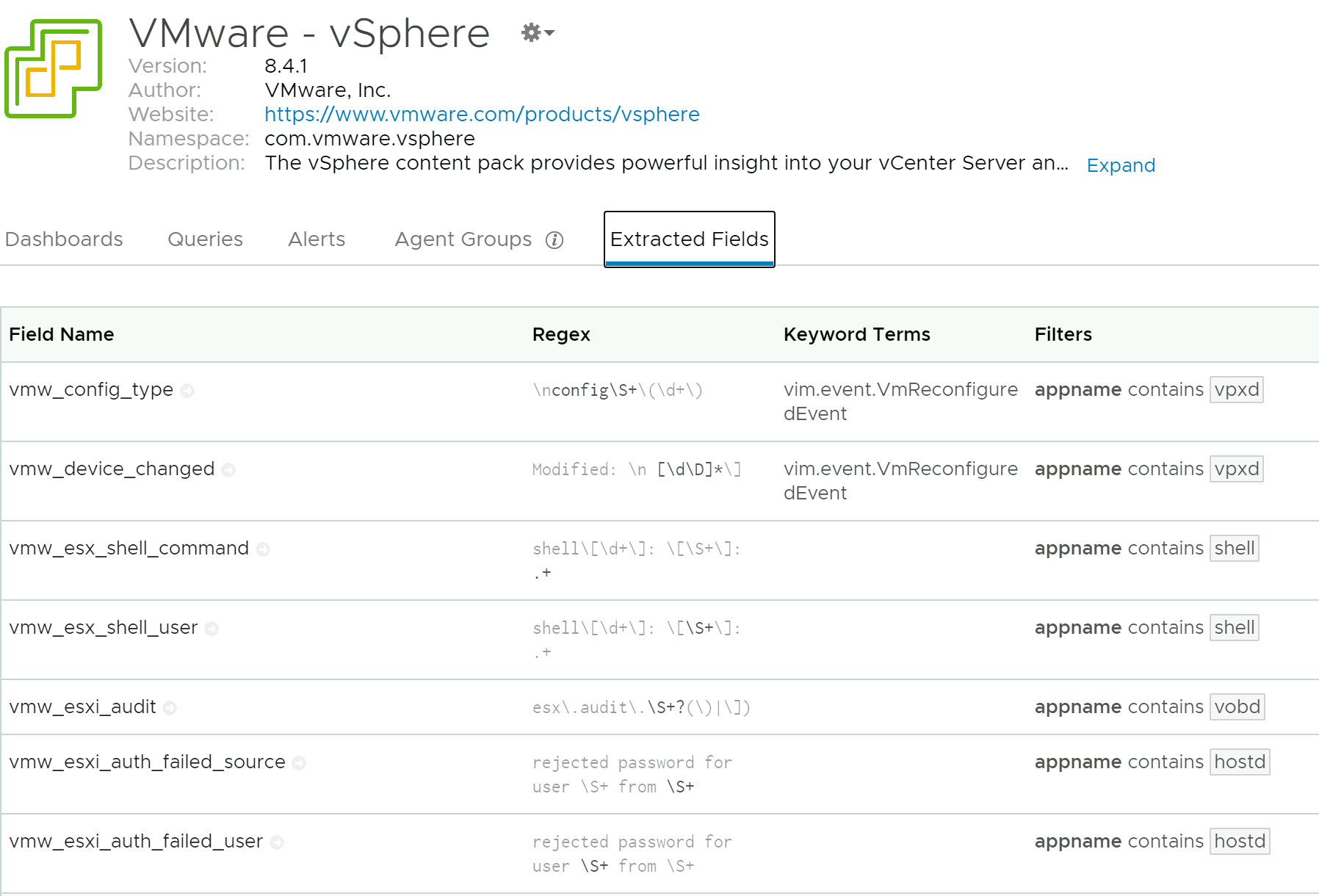
Essentially you can customise to your hearts content - create your own extracted fields containing information import to you! Log Insight makes this easy via the Interactive Analytics page and if you have good RegEx foo then you can achieve lot with customising your own extracted fields.
Custom extracted fields are generally included as part of vendor provided Content Packs. They're used to create dashboards, generate email or even webhook based alerts (into Slack, Teams, PagerDuty or a range of others as listed here). Favorite or save your frequently used queries and share them with others, I'm reasonably new to Log Insight but I think the possibilities here are endless 🤩. With all your key systems forwarding log information to the one place correlating events becomes a lot less challenging.
Agents: Windows and the Linux
Log Insight can also be used to ingest logs from both Window and Linux systems by way of an in-guest Agent. Pre-built packages for Windows (MSI), and Linux (deb, rpm, bin) guests are available and can be fully customized. The Microsoft Active Directory and Microsoft Windows Operating System content packs are good examples designed for use in conjunction with Windows Agents.
Speaking of Windows, Log Insight supports Active Directory sign-on integration and granular access control using AD users/groups. With security being king these days you can never have too much in the way of audit trails. A number of the market place content packs have pre-built dashboards reporting logins, login failures, account lockouts etc, or of course you build your own easily enough.....
Final thoughts 🙌🏼
I think we've only scratched the surface of what we can achieve with Log Insight and have found it a valuable addition to the tool box. Log Insight as a central repository for aggregating logs and real-time data makes analysing events/trends a simple task with its powerful search abilities. Extend this futher with extracted fields and its ability to perform query based alerting and you have something that you'll wonder how you ever managed without.
