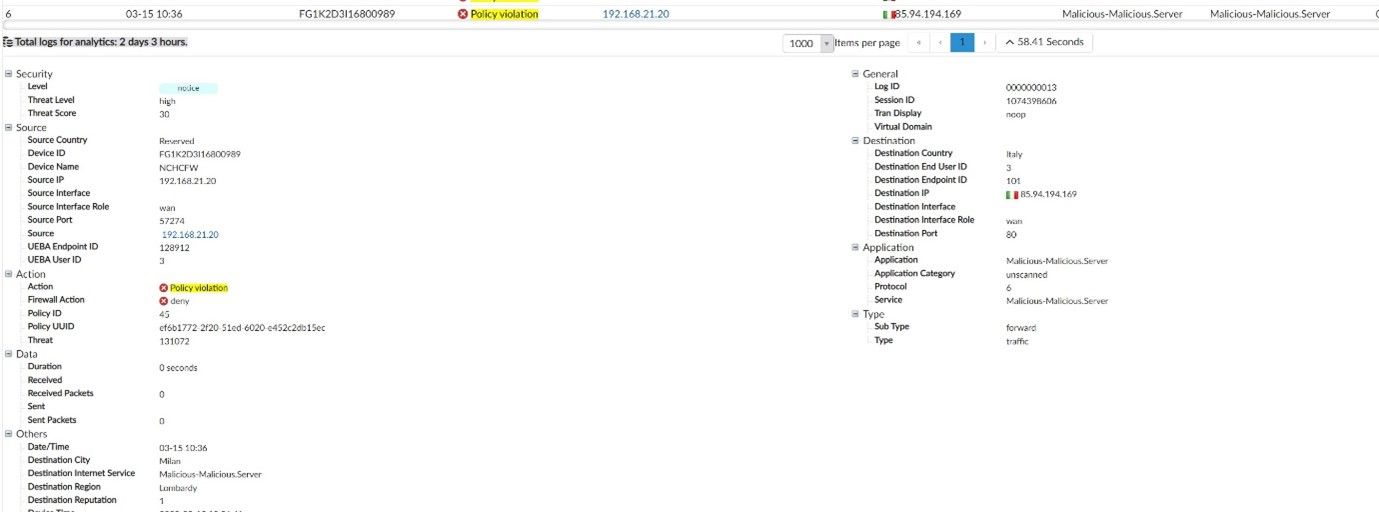
This 1 FortiGate Rule Could Save You
A FortiGate firewalls core functionally is processing traffic with matching rules, thus allowing or blocking traffic depending on the rules you create, so in this blog I’m go talk about creating top security rules for FortiGate's that will improve network security and more importantly is super easy to implement. This rule makes use of the Fortinet IP Reputation Database which is a dynamic list of known bad IP's that Fortinet manages.
Most firewall’s including FortiGate work on rules that are processed top to bottom, this concept is key when creating rules as understanding the rule placement can affect if a rule even gets used. One rule that is effective and simple to create and I recommend to everyone is a top rule that blocks nefarious or malicious traffic using the FortiGate built in ISDB’s. I would recommend creating this rule from Trusted/Internal to Untrusted/Internet with the source set as “all”, destination being the FortiGate built in ISDB’s of “Botnet- C&C.Server”, “Malicious- Malicious.Server”, “Phishing-Phishing.Server” and “Spam-Spamming. Server” with optional being “Blockchain-Cryto.Mining.Pool” and “Proxy-Proxy.Server” then the option of Deny and Log All. Once the rule is created you will need to move the rule (drag and drop) to the top of the zone pair so that all traffic that uses the zone pairs hits the newly created rule. If the rule is placed below a Any to Any on HTTP/HTTPS rule, then the Deny rule may never be hit.
Another rule also worth creating is a block countries, which will look similar but the destinations of known bad act countries such as Russia, North Korea, Iran, service as “ALL” with “Deny”, and again this rule will need to be at the top of the zone pair rule set.
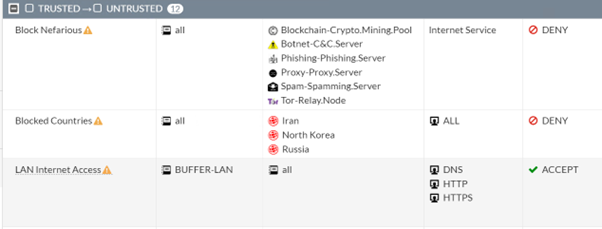
It might be best practice to periodically check that there are no hits against the Deny rules, you will need to have the “Last Used” column visible to show if the rule has a hit. If a hit is present, you may want to look deeper into the logs to ensure that there is no infected or comprised host internal on your network.