Don't be like Okta. Be like Bill
Okta are in the news currently. And not in a good news sort of way.
If you haven't been paying attention, Okta are an authentication company used by thousands of organisations around the world. They have now confirmed an attacker had access to one of its employee laptops for five days in January 2022 and that several of its customers may have been affected — but maintained at the time that its service “has not been breached and remains fully operational.”
The disclosure came as hacking group Lapsus$ posted screenshots to its Telegram channel claiming to be of Okta’s internal systems, including one that appears to show Okta’s Slack channels, and another with a Cloudflare interface.
Any hack of Okta could have major ramifications for the companies, universities, and government agencies that depend upon Okta to authenticate user access to internal systems. They're a gateway to thousands of other systems. There's absolutely no excuse for having left those systems at risk despite knowing that a "limited" compromise of their own systems had occurred.
While a data breach for this organisation is less than ideal (probably an understatement), what has compounded their misery is their handling of this incident, which could be described as 'a bit of a dumpster fire'. In such a way too, that the damage to their reputation, could be just as bad, if not worse, than the breach itself.
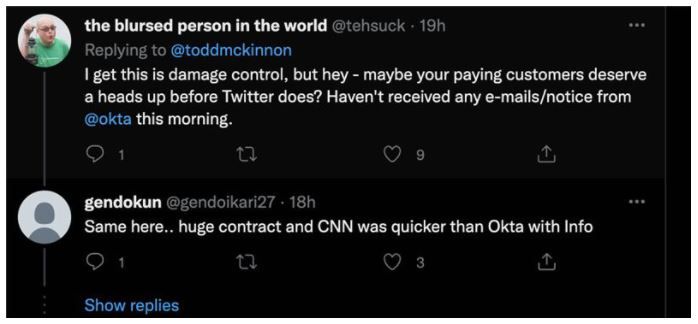
Okta's big failing during this incident has been their communications. They've changed their story several times, from an initial "nothing happened" to "oops, something did happen" and now to "even though something happened, customers were safe, but we're still checking to make sure." While waiting for the forensic investigation to conclude, they should have been proactive and contacted their customers right from the beginning. And if it turned out to be a 'nothing incident' then all good, nothing lost.
All they needed to say was, "hey, we've detected a possible security incident with a third party supplier, we're investigating, but please consider whether you wish to take mitigating actions yourselves, such as resetting your credentials"
Instead they kept quiet and let their customers shoulder the risk. Now they're in damage control, and its not a good look.
Not exactly a ringing endorsement for a provider that's supposed to be part of your first line of defense.
End result - reputation is damaged.
Moral of the story? Compromises and mistakes happen. Even to authentication providers. The conversations with your customers will be difficult and some hard questions will be asked, and you will be run through the wringer that's for sure. It will be unpleasant and awkward for a while, and you may actually lose customers. But you owe it to yourself to front-foot it without any weasel words and obfuscation. That is the best way to come out the other side with reputation intact.
Oh yeah, here is Bill ...

